Azure Synapse Analytics Custom Roles
Recently I had a challenge in terms of providing a least permissions possible security model for a Data Engineer persona when working with Synapse Analytics. I won’t go into detail about all the various permissions that were required and crucially, what the persona was not allowed to do, but I’d like to walk you through the problem and the resolution.
Security Problem
There I am, looking at the inbuilt RBAC (Role-Based Access Controls) within Synapse, and I’m having to add a Data Engineer user to quite a few different roles. Rather than give the user Synapse Administrator permissions, I needed to give the user the following roles just so they could develop Pipelines, create Linked Services, work with Managed Private Endpoints, work with secrets from Key Vault etc. The following roles were required to provided them a good level of access to develop, without hindering too much:
- Synapse Contributor
- Synapse Credential User
- Synapse Linked Data Manager
- Synapse SQL Administrator
As you can see, there is quite a lot there to manage in terms of adding users to roles (actually, it would be adding Active Directory groups to these roles rather than user accounts, but you get the idea).
However, there was a problem…previewing data in a Synapse Pipeline. The Data Engineer couldn’t enable interactive authoring on the integration runtime running in a Managed Virtual Network (VNet).
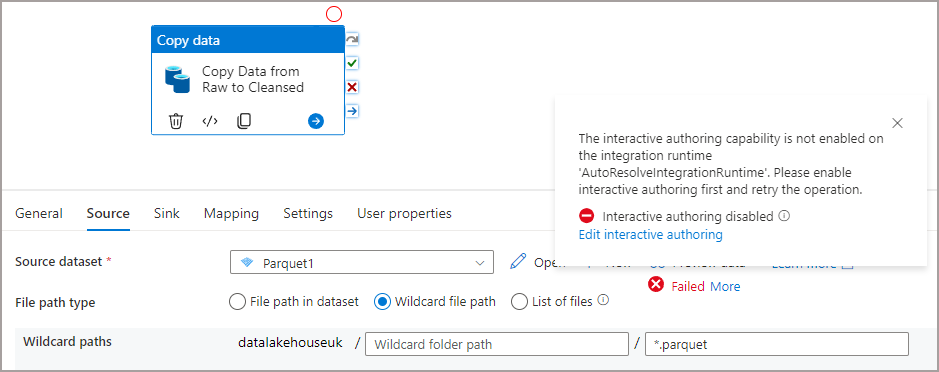
Each time they tried, they received an error stating they did not have access (actual IDs removed):
{"error":{"code":"AuthorizationFailed","message":"The client 'user@mydomain.co.uk' with object id 'b0ae67dc-xxxx-xxxx-xxxx-xxxxxxx' does not have authorization to perform action 'Microsoft.Synapse/workspaces/integrationruntimes/enableInteractiveQuery/action' over scope '/subscriptions/d496ab56-xxxx-xxxx-xxxx-xxxxxxxx/resourcegroups/dhrgqapermissionstest/providers/Microsoft.Synapse/workspaces/actualsynapseworkspace/integrationruntimes/AutoResolveIntegrationRuntime' or the scope is invalid. If access was recently granted, please refresh your credentials."}}
OK no problem I thought, I’ll just go find the relevant Synapse role that has the following permissions in Microsoft.Synapse/workspaces/integrationruntimes/enableInteractiveQuery/action and add the user to that role. I looked through the documentation here and couldn’t find anything related to enableInteractiveQuery. The only documentation I could find was here in the section PIPELINES, INTEGRATION RUNTIMES, DATAFLOWS, DATASETS & TRIGGERS but it suggested that the user would need to be given Owner or Contributor permissions on the actual Synapse workspace itself…a huge no.
Using Custom Roles
I’m not much of a security expert generally in Azure, I know how to lock down data resources, but I’m not familiar with all the various features available…hence I didn’t know about Custom Roles. These allow you to create a role and add in the relevant permissions from a variety of services. Here’s what I did:
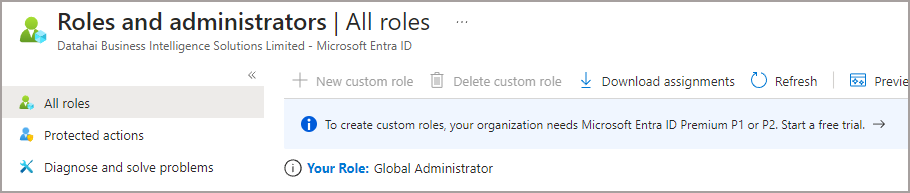
- Searched for Active Directory in the Azure portal…couldn’t find it…then searched for Entra 🙂
- Clicked on Roles & Administrators and was promptly told I couldn’t create custom roles due to licensing:
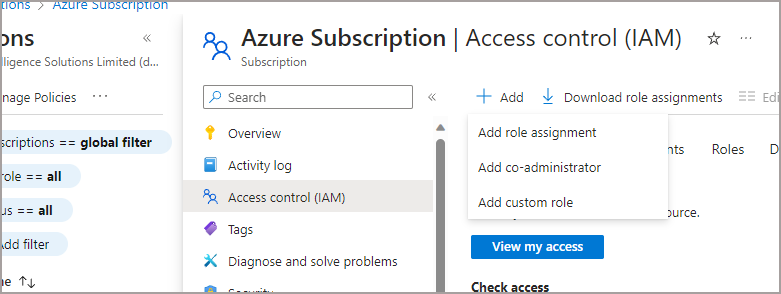
So here’s what I did, but at the Subscription level:
- Click on the relevant Subscription
- Click on Access Control (IAM)
- Click Add -> Add Custom Role
- Give the role a name of Synapse Data Engineer
- Then on the Permissions tab, click Add Permissions
- Click on Azure Synapse Analytics (workspace)
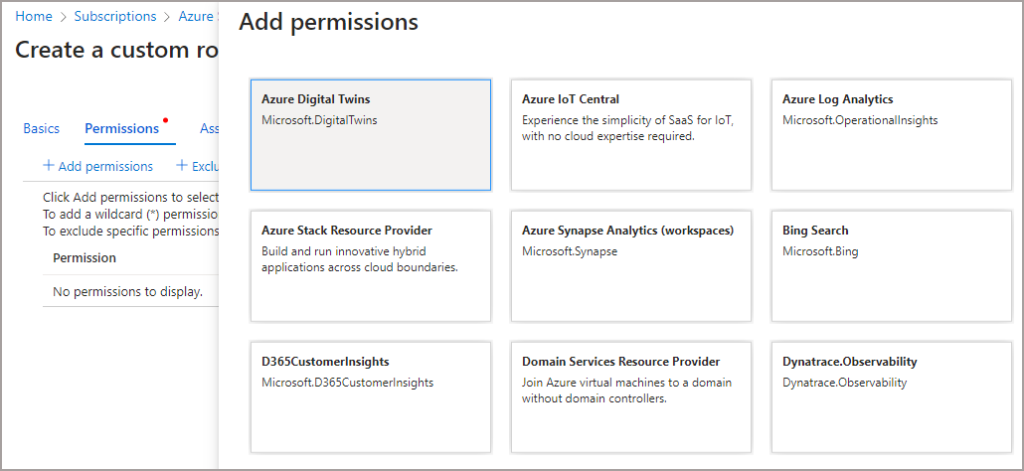
- Search for interactive and there are the granular permissions.
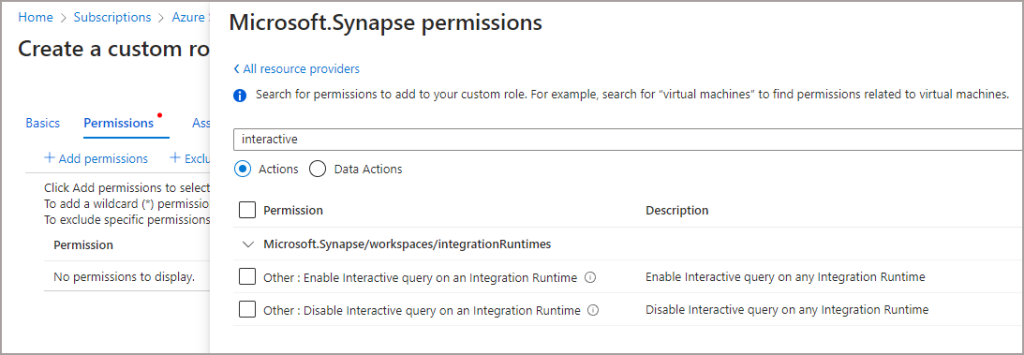
In-fact, there are a lot of granular permissions for Synapse, so you can go through the list and enable the relevant permissions for your custom role. You can then add in permissions from other services too, E.G. reading/writing to Azure Storage. Essentially you are creating a bespoke permissions role tailored to your security posture, I like that a lot.
I could then browse to the relevant Synapse workspace, click on Access Control (IAM) and add the custom Synapse Data Engineer role to the workspace, allowing the Data Engineer to stop/start interactive authoring.
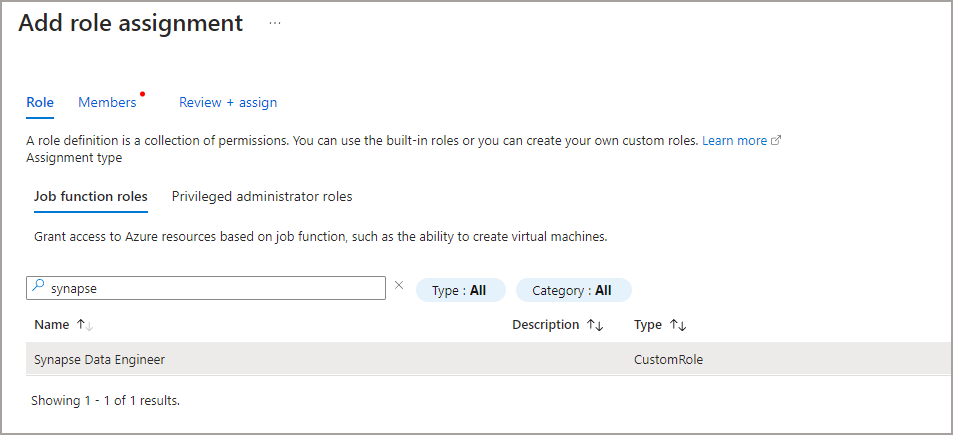
Conclusion
So there we go, Azure Custom Roles are your friend and you can get very granular in the permissions allocated across all the services you need.
By the way, always create another Azure hosted Integration Runtime as you can then configure the interactive authoring time to live setting and reduce it down from the default 60 minutes to 10 minutes – less billing charges!).
As always, feel free to reach out and chat to me about this (or anything Synapse/Fabric related)







